Courtesy of Dot Tech
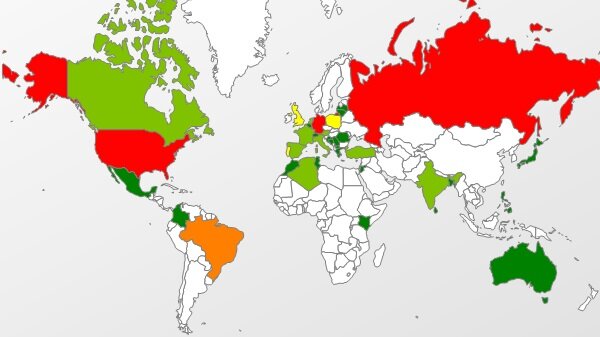
On Saturday, April 26th, Microsoft and security firm FireEye announced that online spies are using an unknown flaw in Microsoft’s Internet Explorer to make targeted attacks. If targeted, attackers can control your computer remotely and they can install more malware without your knowledge. They are called “Zero-Day Attacks.”
So, What is a Zero-Day Exploit?
For those unfamiliar with the term, a zero-day exploit or attack is one that takes place without warning, which is to say that a previously unknown vulnerability is discovered and subsequently exploited. This is because there are zero days between the day the breach is discovered and the day the attack occurs. Depending on the data system breached, this can range anywhere from an inconvenience to a major, worldwide event. There are a number of things each of us can do to protect ourselves, our identities, our finances and our data from a zero-day exploit.
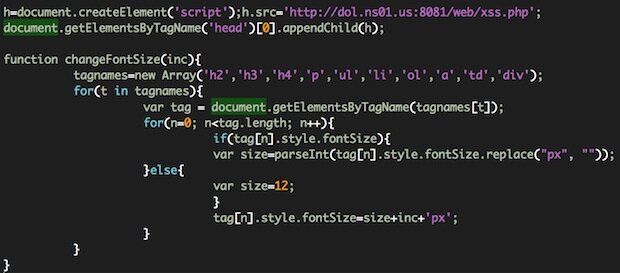
Zero-day attacks can occur from many different sources because individuals writing the malware behind the attacks can release the attacks from several different mediums. Software can be written to attack a wide variety of vulnerabilities and can be delivered in many ways to include email through hardware or through different file types.
How can users protect themselves and their data from these types of attacks? Experts say that the best way to prevent these attacks is to make good decisions about their own information, data and security. Keep it to a multi-layered approach where an attacker would have to work through several different and stand-alone layers of security to breach your data.
The Truth About Servers
The first layer would be security measures on the server you’re using. Server protection is a commonplace tool in the corporate and government world, but many people think that desktop security is enough. Having this added layer of security on the server can be invaluable for repelling a zero-day attack.
Courtesy of Security Affairs
Take Precautions
Next is to install desktop protection software on all machines that access the internet or files that have been used by individuals accessing the internet. After installing the software, it’s critical to keep the software up to date by installing updates immediately when they become available and not letting the security software lapse.
Vary Your Passwords
Finally, take care of your data and always password-protect your data. Use a wide variety of passwords and never use the same one for multiple access points that can adversely impact one another. To illustrate, using the same password for online banking and for a credit card login is not a sound practice. Switch up your passwords and change them frequently to ensure that if one is uncovered, all of your data is not breached.
Zero-day attacks are going to happen and they aren’t necessarily to be feared, but instead respected and prepared for. Spend time educating yourself about all of the measures you can take to reduce your vulnerability to a zero-day exploit. So, how are you equipping yourself for a potential attack? Let us know in the comments section below!
By



Paul W.
Thanks for this article. We live in a crazy world.